Web3 is for enemies
Plus how to mine at home and heat it, too and DAOs are still for crimes
In this issue:
Web3 is for enemies
How to mine at home and heat it, too (reader submitted)
DAOs are for doing (securities) crimes (reader submitted)
Web3 is for enemies
Bitcoiners are fond of saying "Bitcoin is for enemies" which by the standards of Bitcoin culture is actually fairly welcoming. The idea is that Bitcoin is so radically inclusive that no one can be excluded — which means it will inevitably be used by people you find distasteful and there is nothing you can do about it. You will have to tolerate your enemies using Bitcoin for the same reason that they will have to tolerate you: neither of you have any choice. Bitcoin is for enemies.
The cultural analog in the NFT space is probably wagmi (i.e. we're all gonna make it) which is at first much friendlier but kind of breaks down on closer examination. Wagmi sounds nice but doesn’t exactly capture the spirit of a developer rugging a project and stealing the treasury or a scammer tricking someone into giving up their seed phrase. Wagmi is more aspirational than descriptive — if we were really all in it together we wouldn’t need a decentralized ledger in the first place.
In other words, we're all gonna make it isn’t really true. Some people are going to get scammed because no one can exclude the scammers. As web3 matures it is increasingly being forced to confront the truth: web3 is for enemies.
Consider, for example, the story of Brantly Millegan. Until recently Millegan was the Director of Operations at True Names Limited, the company behind the Ethereum Name Service (ENS). By all accounts he was good at his job and well regarded by the community. But in 2016 he did a very bad tweet, which he has since deleted. In the tweet he condemned gay people, trans people, women who have had an abortion and anyone who engages with porn, masturbation or birth control. It was a very bad look.
The discovery of this bad tweet caused a lot of people distress because it is fairly obvious that we are not all gmi if gay people, trans people, women and anyone who enjoys sex is left behind. When confronted Millegan was unsympathetic and stood by his previous views, citing his Catholicism in roughly the same tone as the whale biologist in Futurama. A growing band of people began to call for True Names Limited to fire Millegan which, after briefly resisting, they did.
To a lot of cryptocurrency participants this was "caving to the woke mob" but as a business decision I think it was a pretty obvious one. Gay people, trans people, women who have had abortions and anyone who enjoys sex are all potential customers. A senior executive that alienates potential customer bases is terrible for business. It isn’t exactly rocket science.1
How to mine at home and heat it, too
"I would be interested to see a review of the economics of electric heaters that could instead be mining BTC and be using their waste heat for heat. E.g. in homes, electric cars, etc ... Seems like double dipping could happen when you're already planning on using electric heat elements." — AS
Bitcoin miners are just specialized computers and like any other computers they overheat when they work too hard. The difference is that Bitcoin miners are always working as hard as they possibly can, so they are always overheating. For large scale mining operations that’s a major drawback — much like traditional data centers they often need to pay to keep their machines cooled.
Smaller operations can actually take advantage of this waste heat by using it to heat their homes or whatever room/building they are mining in. In a theoretical sense that gives them an opportunity to be more cost-efficient than larger scale operations (since they benefit from the heat rather than have to pay to remove it) but in practice the cost of heating or cooling is a rounding error next to the cost of electricity itself and larger operations can usually negotiate better wholesale electricity rates.2
So as a means of mining Bitcoin it realistically doesn’t change the economics very much — but what about if you were already planning to use an electric space heater? Wouldn’t it be nice if that space heater also earned a little bitcoin on the side, even if all it did was give you a small rebate on your heating costs? It could even come in a sleek design in your choice of white or orange-and-black.
The truth unfortunately is that just as this is probably just as bad a strategy for heating your home as it is for mining bitcoin. First of all mining rigs are loud. Like, really loud. You could run them less loudly but they would produce both fewer bitcoin and less heat so it would somewhat defeat the purpose. Mining rigs are also not great heaters. They do give off heat but much more slowly than an electric space heater and with much less control.
A typical space heater off of Amazon costs $30-100, heats quickly, is relatively quiet and lets you dial the heat up or down. The Heatbit miner from the tweet above sold as a pre-order for $1000-1200 and has none of those features. How much of a discount on heating you will get for these compromises is an open question — the Heatbit website has a handy little calculator to let you play with assumptions but it ignores the most important assumption of all: how much the mining difficulty will grow.
The lifecycle of a typical space heater is years but the lifecycle of a typical Bitcoin miner is much shorter than that. As the network grows more miners are competing for shrinking rewards and the revenue for any given quantity of hashrate quickly disappears. It would not be very long before you were left with a loud, inefficient space heater that earned effectively nothing.
There will always be hobbyists who enjoy running their own Bitcoin miners in the same way people enjoy brewing their own beer. It can be fun and rewarding but it is almost certainly cheaper to pay professionals to do it for you.
DAOs are for doing (securities) crimes
I do indeed think that DAOs are for crimes! People are often surprised by that. But I think the argument is pretty straightforward — DAOs are much more expensive to operate than traditional organizations like S-Corps or 501c3s. So for any given DAO it’s worth asking, why is it worth paying to decentralize this? When you ask that question carefully I think it’s pretty clear the answer is always crime.
FriesDAO is a DAO that is raising funds to buy a McDonald’s franchise, a reference to the meme about failed crypto traders needing to get a job at McDonald’s. LinksDAO is a DAO that is raising funds to buy a golf club. Run properly neither a McDonald’s franchise nor a golf club is a criminal enterprise — but then again you don’t need a DAO to do it. Most golf clubs and fast food franchises do not rely on blockchain governance to manage their operations.
You don’t need a DAO to buy or run a legitimate business. But you do need a DAO if you want to sell shares in your business to small investors. Banks won’t let you do that, because it is illegal. To be legal, a securities offering must be registered with the SEC and will generally need to be restricted to accredited investors. Raising lots of money quickly from small investors is very difficult to do in the traditional financial system, but it is easy for DAOs because DAOs are for doing crimes.
Financial law is interesting because financial criminals are tricky in a way that most criminals are not. Murderers will try not to get caught obviously, but they generally do not try to convince you that what they actually did was bundle a survival-default-swap and previous regulations do not apply. Financial criminals on the other hand play semantic games like that all the time, so financial law has to be written both very carefully and very broadly to avoid any wiggle room.
FriesDAO and LinksDAO are very aware that they are skirting the law and work hard to assure you they are not a security. FriesDAO refers to buying tokens as a 'donation' and promises only 'governance rights'. LinksDAO refers to tokens as 'membership cards' and promises 'exclusive perks'. Both projects emphasize that the token does not entitle the owner to any share of the profits. No securities here, officer!
Renaming securities to something else and disguising the profits as benefits is not a new trick, though. There is actually already specific court precedent ruling that memberships in a golf club that doesn’t exist yet are securities. That’s why LinksDAO had to be a DAO and not a Kickstarter. DAOs are for doing crimes.
Other things happening right now:
We spoke recently about how harshly the regulators have been treating crypto companies attempting to work within the system as opposed to simply ignoring it entirely. Case in point crypto lending company BlockFi is rumored to face ~$100M in fines from the SEC:
The folks who build front-running bots to exploit MEV are in a sense locked in zero-sum combat with each other. Each opportunity to prey on an ordinary transaction can ultimately only be harvested by one predator. Still there is a kind of mutual respect between elite competitors of any kind. This week two anonymous MEV bot runners left notes on the blockchain saluting each other as comrades-in-arms and celebrating their competition. A bit like two snipers pausing in a firefight to compliment each other’s aim.
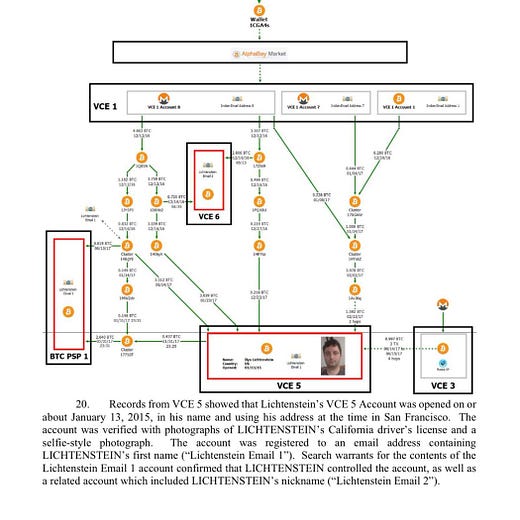
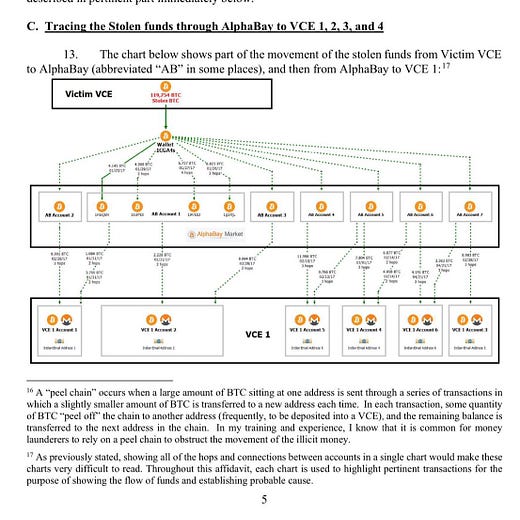
We spoke recently about the $4.5B heist by wealthiest rap artist in history Razzlekhan and her husband. Shockingly the two don’t seem to be master hackers — instead it seems like the actual security breach was the result of social engineering. This is a story about crime with Bitcoin but it isn’t a story about how Bitcoin is great for crimes. The couple stole ~120k BTC but the government was able to seize ~90k BTC. Over 5 years they were only able to liquidate ~1/4th of their loot and they got caught. It turns out using a permanent, public ledger is a bad way to launder stolen money. Not legal advice.
True Names Limited is actually technically a non-profit that supports development of ENS but the goal is still ultimately to attract customers to the ENS network.
In the long run I suspect most mining rigs will be run under fluid baths that capture and reuse waste heat and the hobbyist advantage here will disappear. But we’re a long way from that world today.









Broken link for "the actual security breach was the result of social engineering", I'd love to read about how the attack was carried out.